- 24x7 live Support
- (202) 769-5123
That’s the harsh reality of modern cyber defense—and it’s why even well-resourced organizations are getting breached.
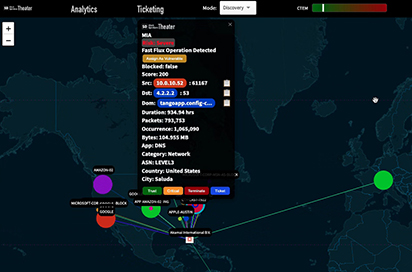
The Emergency Cyber Response Health Check offers a fast, non-invasive, and low-cost way to scan your environment using the Streaming Defense Attack Operations Theater (SD-AOT). In just hours, it can uncover anomalies, silent threats, and blind spots that legacy tools may miss entirely.
If any of the following statements apply to you, a Health Check is not optional—it’s essential.
1. You do not have real-time visibility into your network.If you’re relying on logs and delayed reports, you’re already behind the adversary.
2. You do not currently detect anomalies or outlier behavior in network traffic.If your tools only alert on known threats, attackers who "live off the land" will remain invisible.
3. Your security tools haven’t found anything concerning in a long time. That’s not always a sign of safety - it could be a sign of blindness.
4. Your network seems slower or is exhibiting unusual behaviors.
Unexplained delays could signal lateral movement, scanning, or beaconing.
5. You allow personal devices (BYOD) to connect to the network.
Even with basic endpoint protections, unmanaged devices introduce serious risk.
6. You have not conducted a live traffic assessment in the past 12 months.
If you’ve never seen your network traffic animated in real time, you may be missing everything.
7. You’re about to sign up for or renew cyber insurance.
Find out what underwriters may uncover—or worse, deny coverage for—before they do.
8.You’re connecting with a new supply chain partner.
A single compromised vendor can become a backdoor to your environment.
9. You’re about to sign an Interconnection Security Agreement (ISA).
A clean bill of health can demonstrate diligence, or flag areas to remediate before signing.
10. You’ve had network changes, upgrades, or vendor maintenance recently.
Even routine patching and config changes can leave behind unintended vulnerabilities.
11. Your LAN, server room, or infrastructure areas were recently found unlocked or open.
Physical access can lead to network implants or rogue devices that evade traditional detection.
12. You’re preparing for a third-party or government penetration test.
Identify weak spots and fix them before they’re exploited in a live evaluation.
13. You rely on SIEM, EDR, or firewalls—but not full network visibility.
These tools are vital, but attackers often slip through them. Full packet visibility fills the gap.
14. You’ve experienced unusual outbound traffic patterns or blocked connections.
Even if blocked, attempted connections to foreign adversaries should be investigated.
15. You recently onboarded or offboarded a contractor or third-party IT support firm.
Changes in access rights or the transfer of privileged accounts may create unexpected risks.
16. You’re consolidating networks after a merger, migration, or office relocation.
Network integration is a prime time for adversaries to exploit overlooked exposures.
17. You suspect that legacy systems are still exposed or unsupported.
End-of-life software and hardware often carry unpatchable vulnerabilities.
18. You’re in a regulated industry with mandatory controls for continuous monitoring.
A Health Check validates readiness, compliance, and internal visibility - all at once.
Emergency Cyber Response is more than visibility - it’s an active defense platform:
 A live view of your network’s current activity
A live view of your network’s current activity Detection of anomalies, lateral movement, and beaconing
Detection of anomalies, lateral movement, and beaconing  Validation of whether threat actors are present or communicating outbound
Validation of whether threat actors are present or communicating outbound Insights into policy gaps and vulnerable services
Insights into policy gaps and vulnerable services No software agents required - completely non-invasive
No software agents required - completely non-invasiveA Health Check can be completed in just a few hours with minimal disruption. It’s the fastest way to confirm you're secure—or uncover what’s hiding in plain sight.
PURCHASE your Health Check Today or CALL NOW or FILL OUT THE FORM
or Pay by Phone
Health Check
Privacy Policy Terms of Service
Beyond Detection - Full-Spectrum Support When It Matters Most.
Develop an attorney-client relationship with specialized cyber law counsel well in advance of a serious incident. Enveloping investigative data with privilege is critical in litigation.
Establish a pre-incident relationship to have a ready team experienced in digital forensics and incident response to investigate, contain and remediate a serious cyber-attack.
Third-party insurance experts providing industry leading and affordable insurance for cyber-related exposures and expenses including data breaches, legal defense costs, ransomware attack assistance, and system disruption recovery.
Continue Reading...