- 24x7 live Support
- (202) 769-5123
Modern cyber threats move in milliseconds - and so do we. The Streaming Defense Attack Operations Theater is engineered to detect malicious activity within seconds of network observation, eliminating the delay between compromise and discovery that adversaries count on.
Every packet is analyzed in memory at wire speed, ensuring that nothing slips through the cracks. From zero-day exploits to encrypted data exfiltration, our AI-driven engine flags threats the moment they appear, with no reliance on slow log aggregation or third-party analysis delays.
Our detection engine goes beyond static indicators of compromise. It uses real-time behavioral analysis, protocol baselining, and dynamic threat modeling to recognize anomalies like lateral movement, insider threats, ransomware, and command-and-control traffic — even when attackers hide in encrypted streams.
Streaming Defense provides immediate geospatial visualization of all threat activity. You’ll see who’s talking to what, where the traffic’s going, and whether it’s safe — in real time. This enables instant situational awareness and supports decisive response actions.
Alerts from Streaming Defense come prioritized and enriched, not buried in noise. Each detection includes context: source/destination, time series, MITRE mapping, and recommended response actions — empowering analysts to act quickly with confidence.
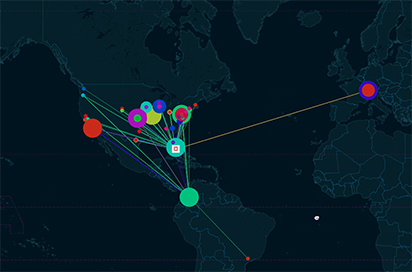
Threats don’t respect boundaries, so neither do we. Streaming Defense monitors:
 IT networks
IT networks OT/SCADA systems
OT/SCADA systems Cloud environments
Cloud environments Remote endpoints and supply chain touchpoints
Remote endpoints and supply chain touchpointsFrom core data centers to field-deployed sensors, we see the entire attack surface as it happens.
The faster you detect, the more you control. By identifying threats in seconds, Streaming Defense drastically reduces attacker dwell time, minimizing damage and maximizing recovery speed. In crisis or peacetime, speed saves missions.
Don’t just detect the threat — beat it to the next move.